The Ultimate Google Workspace Security Checklist
February 10, 2022These days, data can be accessed and compromised in the most unbelievable ways. While this is a growing concern amongst companies, the key to minimising risk is staying up-to-date with the best practises and latest features.
This week, Damson Cloud’s Fintan Murphy walks us through the ultimate Google Workspace security checklist, specifically for medium to large organisations.
Basically - if you manage or belong to a group of IT administrators who safeguard over 100 users - then this video is for you!
What We’ll Cover in This Security Checklist
While this is a checklist, we see it more as a comprehensive guide to help keep your company right at all times. We highly recommend that you bookmark this video and blog post so you can easily refer back to it, or even use it as part of your in-house training programme.
If you require further support, we can also provide security workshops where we examine your organisation’s existing standards, while also identifying new ways you can maximise the safety of your information.
In this ultimate checklist, we will cover the following key topics:
- Best Practises for Administrators
- Account Security Settings
- Security Apps for Google Workspace
- Google Calendar
- Google Chat and Classic Hangouts
- Google Chrome Settings
- Device Management
- Google Drive
- Gmail, Google Groups, Sites and Vault
Let’s dive in!
Best Practises for Administrators
IT administrators for medium and large businesses should follow these best practises to help strengthen the security and privacy of company data.
Setting up two-step verification on all user accounts is pivotal and so easy to implement into your organisation’s day-to-day operations. It essentially protects an account from unauthorised access by giving back user control and adding an extra layer of security when completing certain actions on Google Workspace. This could be verified via email, text, phone and other methods.
We highly recommend enforcing the use of security keys, whether they be digital or physical. Security keys are small hardware devices used when signing in that resists phishing. This should be implemented at least for admins and other high-value accounts. One app that we suggest our customers look into is Smart Lock, which protects and stores your passwords and security codes without needing to remember them every time you login.
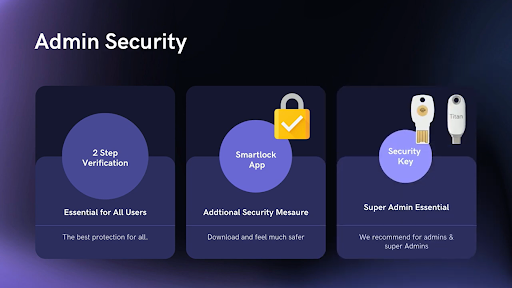
Another piece of advice we give to all of our customers is make sure you don’t share accounts! Instead, separate your super admin, admin and day-to-day accounts. It’s better for traceability and accountability should you need to monitor something that has been actioned on an account. Google Cloud Identity is particularly useful - it is basically a unified identity, access, app and endpoint management platform that gives users easy access to apps with single sign-on should they need it.
Account Security Settings
In Google Workspace, there’s various ways you can to boost the safety of your organisation’s accounts through security settings.
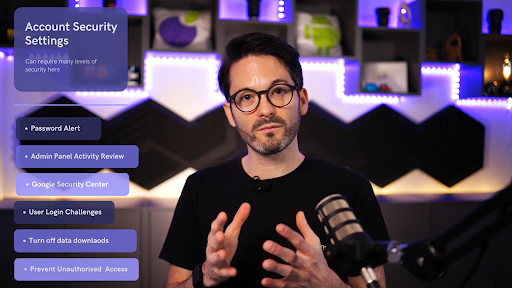
One of the most common pieces of advice you’ll have heard is choosing a strong, unique password. A good password is the first line of defence to protect user and admin accounts alike. Its also best that you keep passwords different across other accounts such as email and online banking. Password Alert is a handy tool that can help prevent password reuse. When you add Password Alert to your Chrome browser, you’ll get automatic alerts when your Google password is used to sign in to non-Google sites.
To help prevent and remediate compromised accounts, you should regularly review activity reports and alerts for account status, admin status, and two-step verification enrollment details.
Adding user login challenges is a great way to spot suspicious activity. It works whereby users must enter a verification code that Google sends to their recovery phone number or email address, or else they must answer a challenge that only the account owner can solve.
Turning off Google data download helps if an account is compromised or the user leaves the company. It essentially prevents said user from downloading all their Google data with Google Takeout. Another action you can take is revoking a user’s access once they leave.
Security Apps for Google Workspace
Security apps can add great value to your Google Workspace environment, especially when it comes to protection. However, you should always make time to review how exactly they are helping your organisation.
Here’s a handful of tips we offer all of our customers:
- Review and approve third-party apps so you know which ones can access Google Workspace core services such as Gmail and Drive
- You can also create a list of these apps you trust and circulate them to staff so there is no chance of someone downloading an app that they shouldn’t
- Block access to less secure apps, especially ones that don’t use modern security standards, such as OAuth, as these can increase the risk of accounts being compromised
- Control access to Google core services: you can allow or block access to Google apps such as Gmail, Drive, and Calendar based on a device’s IP address, geographic origin, security policies, or OS
Google Calendar, Chat and Hangouts
Calendar and Chat are two central methods of communicating with people both internally and externally. Because of this, they can pose certain risks which should be mitigated via the following tips:
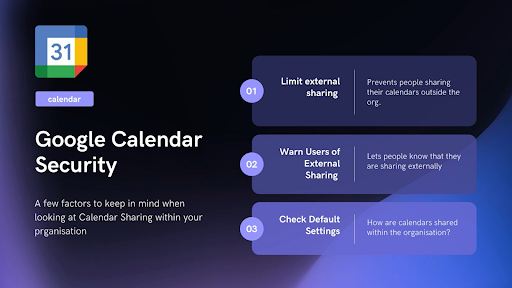
Where you can, limit external calendar sharing. This doesn’t mean you have to hide all of your information. Instead, you can simply restrict external calendar sharing to free/busy information only. This is especially important for reducing potential data leaks.
Google Calendar comes with a default setting that also warns users when they invite external guests. You should take a look at what other default settings are available in Calendar, and assess how these can be tailored to better suit your business.
For example: one default is that employees can see each other’s calendars - but this shouldn’t be the case for the likes of higher management. This is because we have seen it happen before where a confidential document link is placed in a calendar event, and staff can therefore access information that they shouldn’t.
As such, you should set permissions correctly as soon as possible, as the change isn’t retrospective and doesn’t apply to calendar events that have previously take place.
With Chat, you can restrict the ability to message externally, warn users, or set an invitation policy.
When restricting, you should allow only the users with a specific need to send messages or create rooms with users outside your organisation.
With classic Hangouts specifically, you can warn users when they chat with people outside their domain. When enabled, group chat conversations are split when the first person from outside the domain is added to the discussion.
Setting a chat invitation policy helps determine which users can automatically accept chat invitations based on your organisation’s policy on collaboration.
Google Chrome Browser Settings
In Google Chrome, there’s a vast array of browser settings that can help strengthen your organisation’s security. Here’s a couple of simple ways you can leverage the browser to keep your data safe:
By keeping Chrome browser and OS updated, you can enforce security patching which corrects errors and addresses vulnerabilities in computer software code.
You can force a relaunch to apply updates, where Chrome browser and OS devices can be set to notify users that they need to restart in order to ensure the new upgrade is complete.
To have basic Chrome browser and OS device policies implemented, set the following policies in your Google Admin console:
- Allow password manager (this should be allowed by default)
- Set Safe Browsing to ‘Always enable’
- Prevent users from proceeding to malicious sites (don't allow users to bypass Safe Browsing warnings)
There’s also several advanced Chrome browser policies that help prevent unauthorised access, dangerous downloads and data leaks between sites by setting the following advanced policies:
- AllowedDomainsForApps: allow access to your organisation's Google services and tools only for accounts from the domains you specify
- DownloadRestrictions: block malicious downloads
- SitePerProcess: enable so that each site in Chrome browser runs as a separate process. With this option, even if a site bypasses the same-origin policy, the extra security will help stop the site from stealing users’ data from another website

Device Management
Device management is a huge topic area that we plan to cover in its very own video and blog post. However, for the purpose of this vlog, we will briefly skim over it and highlight what’s possible to achieve:
- Require passwords
- Lock and wipe corporate data
- Manage android apps
- Device encryption
- Apply device restrictions
- Block compromised devices
- Enable auto account wipe
- Block dangerous android apps
- End-point management
- Restrict drive sync tool
- Set up GCPW (Google Credential Provider for Windows)
- Limit privileges
- Context aware access
- Control Google Workspace apps
- Data Loss Protection (with new updates coming soon for Labels in Gmail)
For more information on device management security features, in the meantime you can visit Google’s support page.
Google Drive Security
As Google Drive is a one-stop online storage solution where users can share and access files for the purposes of collaboration, it is essential to vet the settings to ensure data is highly secured. You can do this in a few simple steps, such as:
You can confine file sharing within the boundary of your domains by turning off sharing options. If sharing is required outside of a domain because of business needs, you can define how sharing is done for organisational units, or you can designate domains on your ‘allowlist’.
Similar to Calendar, you should set a default for link sharing that abides by your company’s policies. This can include turning off link sharing for new files, where only the file owner should have access until they decide how to share the file.
You can automatically warn users when they share a file outside your domain. Through this, the user is prompted to confirm whether this action is intentional or not. This does great work in reducing the risk of accidental data leaks.
When a user shares a file via a Google product other than Docs or Drive (for example, by pasting a link in Gmail), Access Checker can be set up so only recipients can open it. This gives you greater control over the accessibility of links shared by your users, all while reducing risks in the process.
You can request external collaborators to sign-in to Google before accessing a particular file. If they don't have a Google Account, they can simply create one at no cost.
For shared drives, you can decide to allow only users in your organisation to move files from their shared drives to a Drive location in a different organisation. Plus, you can restrict who can create shared drives, access content, or change the settings for new shared drives so you have complete control.
Data leaks can be reduced by disabling access to offline docs. When docs are accessible offline, a copy of the document is stored locally. Therefore, if you have a business reason to enable access to offline docs, you should activate this feature per organisational unit to minimise risk.
Installing additional features for Google Docs from the add-on store can cause risks. Because these add-ons are so easy to install and seem to be officially approved by Google, this may lull users into a false sense of security that they are as safe as using Google Workspace itself, but in fact, third-party add-ons can introduce new security risks into your organisation. To support a specific business need, you can deploy certain add-ons for Google Docs that are aligned with your company policy or avoid them entirely.
Setting up Data Loss Protection rules to scan files for sensitive data and take action, as a result, can help reduce risky data leaks. For example, you can warn and even block external sharing of documents that contain passport numbers and get an email alert.

For the rest of our Google Workspace security checklist, check out our video in full at the top of the page or head over to our YouTube channel!
As a longstanding member of the Google Cloud Partner Program, Damson Cloud specialises in bringing people and ideas together through new ways of working. We champion the very best practises in remote working and change management, helping companies and their teams collaborate productively from anywhere in the world. To find out more about our services, check out our library of tutorial videos or our blog.
