Gmail Authentication: A Google Administrators Guide
February 8, 2024Understanding Gmail Authentication: A Google Administrators Guide
Today we have a special treat for you as we dive into the important areas of Gmail authentication with one of our experienced Google Cloud Support engineers, Mark. In this blog post, we'll look at the admin level functions of Gmail authentication, focusing on key elements like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
As usual the video will go into greater detail, so to view that in its entirety see that below on our YouTube channel.
Authentication is vital for Gmail administrators to prevent their businesses' email from being marked as spam and to reduce the risk of spammers impersonating their domain or organisation in fraudulent(AKA Spoofed) emails.
So let’s look at the main points of what SPF, DKIM and DMARC are, starting with SPF.
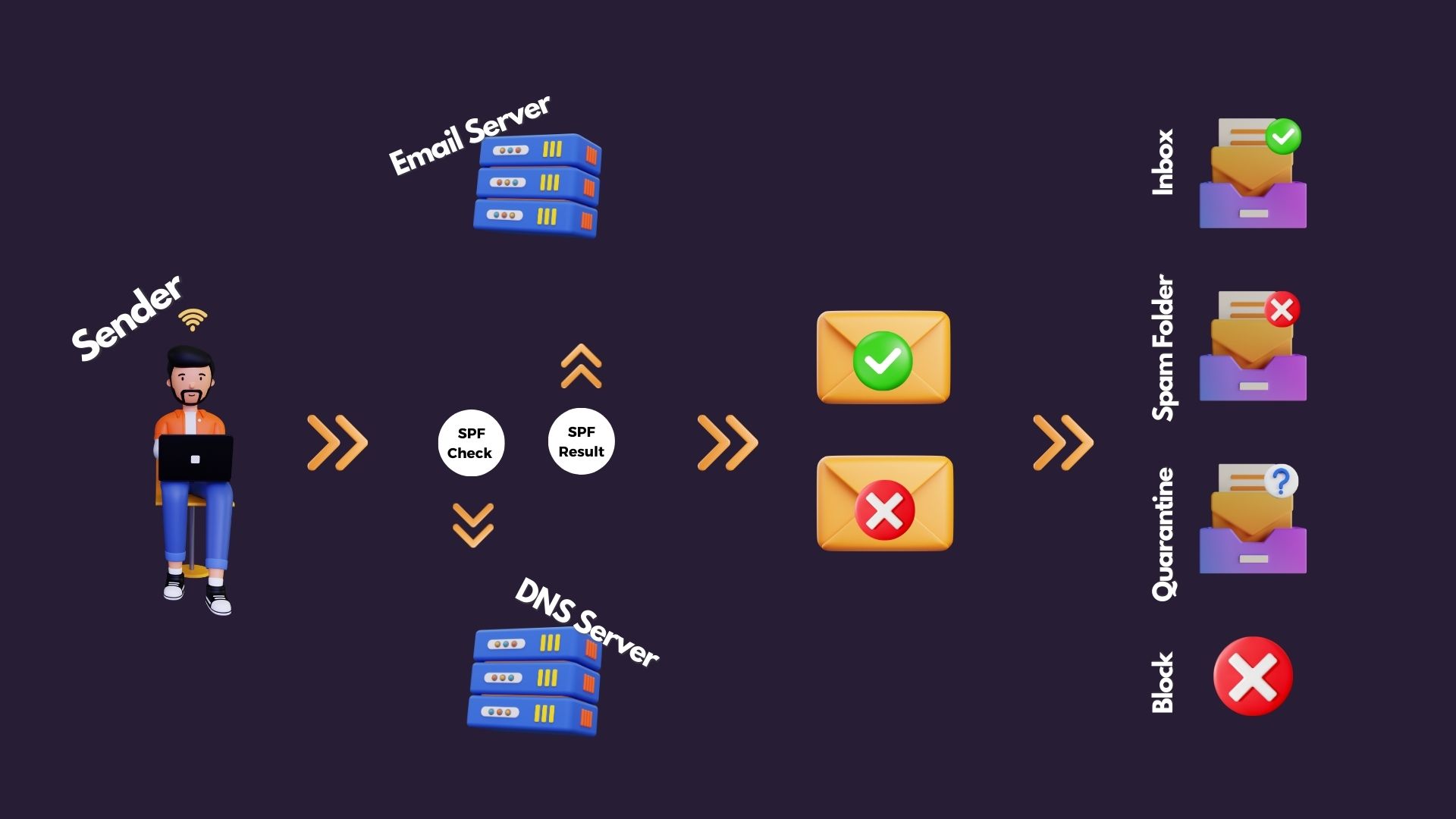
SPF - Sender Policy Framework
How SPF works
SPF, an industry-standard authentication method, identifies mail servers and domains allowed to send emails on behalf of your domain. The SPF record allows the receiving mail server to verify that the incoming message is sent from an approved server. The receiving server can react accordingly to allow mail to be received, sent to spam, quarantined or blocked.
Avoid multiple SPF records to prevent mail issues such as spam or rejection. SPF records are added to the DNS with your DNS provider, keep in mind that it may take up to 48 hours for SPF authentication to start working.
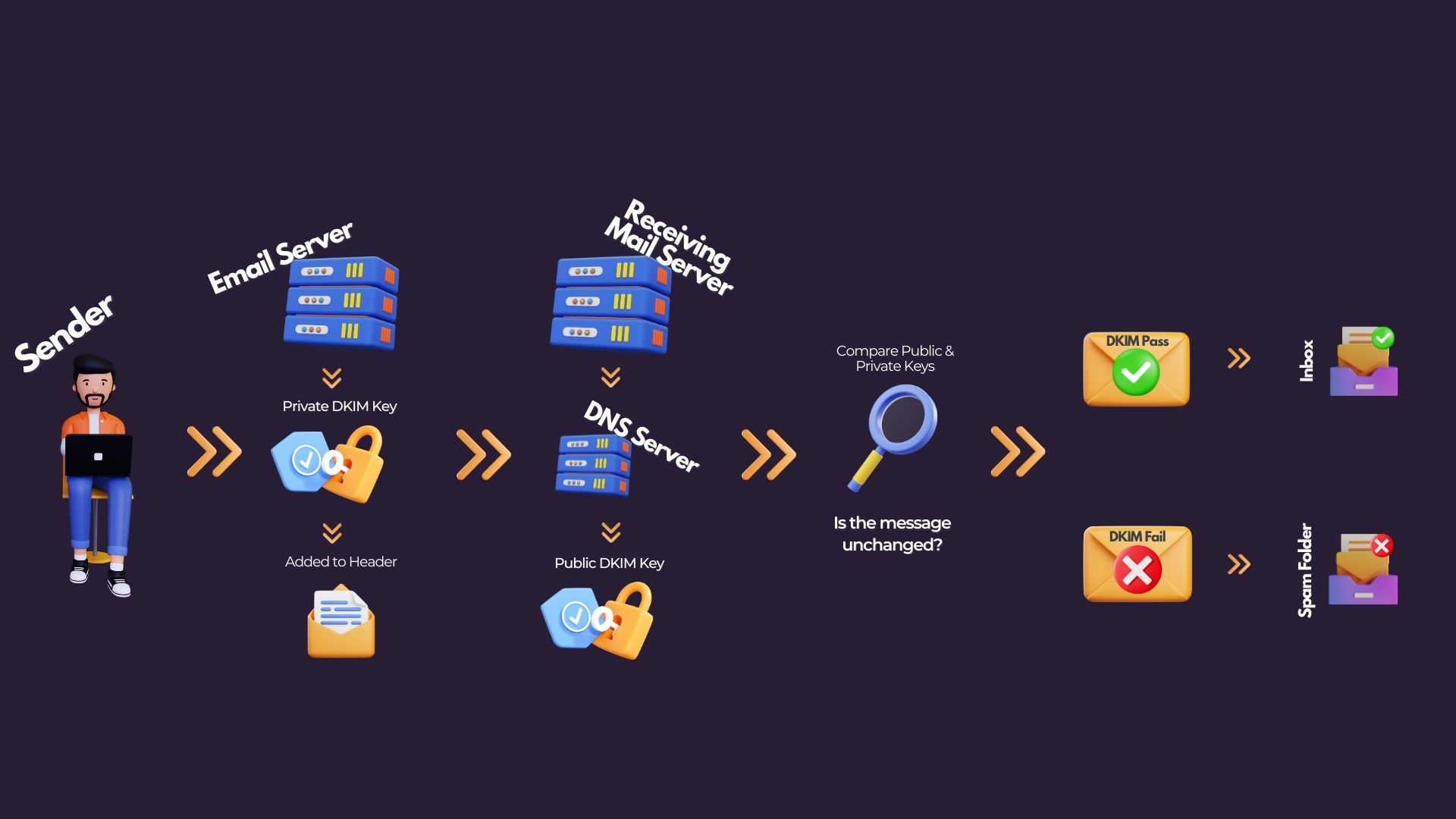
DKIM - DomainKeys Identified Mail
DKIM adds a digital signature to outgoing messages, helping protect your domain from spoofing and preventing outgoing emails from being marked as spam. DKIM can detect when a message has been edited post send or when an unauthorised change has been made to the “From:” address
How DKIM Works
When an email is sent from your organisation, the email server creates an encrypted hash, signs it with the domain's private key, and attaches it to the email header. The receiving server then creates a hash based on the message’s contents as received and signs it with a private key provided from the DNS server. DKIM verifies the message's authenticity by comparing the receiving server’s hash with the original hash attached to the email header. Any difference here indicates that the message may have been changed post send and the message will fail DKIM. Conversely, if they match the message will pass DKIM.
DMARC - Domain-based Message Authentication, Reporting, and Conformance
Preventing Spoofing and Phishing with DMARC
DMARC informs receiving mail servers how to handle messages that don't pass authentication checks. It is crucial to use DMARC in conjunction with SPF and DKIM to avoid mail flow issues.
Setting up DMARC
A DMARC policy record is a line of plain text built from “Tags” and “Values”. These tags inform the system how to apply DMARC to messages. Instructions will include
- Actions to take if messages cannot be authenticated
- What percentage of mail to apply DMARC policy to
- Where to direct reports about DMARC activity
- How strictly to apply the SPF/DKIM policy
The video breaks down how to define the DMARC records in more detail around 6 minutes in so be sure to check that out for more information on how to build your DMARC record
Considerations and Best Practices
- Use reports to monitor DMARC effectiveness.
- Set up a dedicated inbox for DMARC reports.
- Adjust the percentage of messages subjected to DMARC based on your deployment strategy.
To Conclude
In an era where email sender guidelines are tightening, together with legislation on spam and phishing attempts becoming more stringent, safeguarding your organisation's emails is vital for 2024. By implementing SPF, DKIM, and DMARC, you not only protect your domain but also ensure your emails reach recipients safely.
We hope that helps you understand the tools you have available to ensure that your messages get to your recipients safely and are protected from spoofing and phishing. The presence of these safety checks can help safeguard your organisation’s internet reputation and that your domain is trusted by your recipients.
If you're keen on learning more about best practices for deploying DMARC policies or exploring other Admin panel features, check out our Admin Academy, our Google Admin Panel learning site. Additionally, if you're interested in a comprehensive security review with our highly experienced team of Google Workspace engineers, feel free to get in touch here.
As always we’d love to hear from you – if this Google Administrator guide has been useful and you need more tips then please do let us know!
